Redeployment via CI/CD pipeline
In this section, you will update source code in Eclipse, overwriting Hello World! microservice sample and replace it with the code of FlightService. Then, you will commit the code changes to CodeCommit to enable deployment to your AWS Lambda environment and update the Amazon API Gateway configuration to match.
Add microservice code to new branch
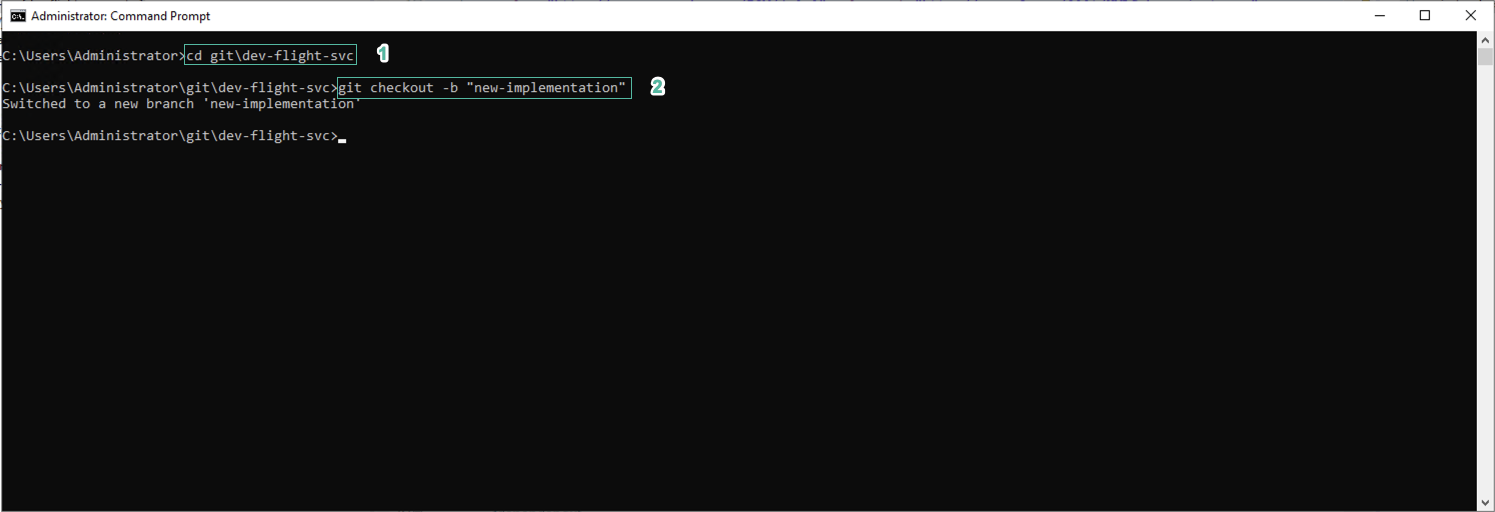
- Move the path to the root of the CodeStar Project we just imported. Use the following command to create a new branch:
cd git\dev-flight-svc
git checkout -b "new-implementation"
- Download the program source code FlightSpecials and extract it.
- FlightSpecials.zip (8525 ko)
- In Eclipse IDE, right-click on the project. select Show In and select System Explorer.\
- Copy the contents of the FlightSpecials folder to the opened folder. You need to delete the content in the two folders /src and /target of the sample project before copying over it.
If you do not delete the contents of the /src and /target directories before copying the new code, the build process will fail because we do not configure HelloWorldController / Handler.
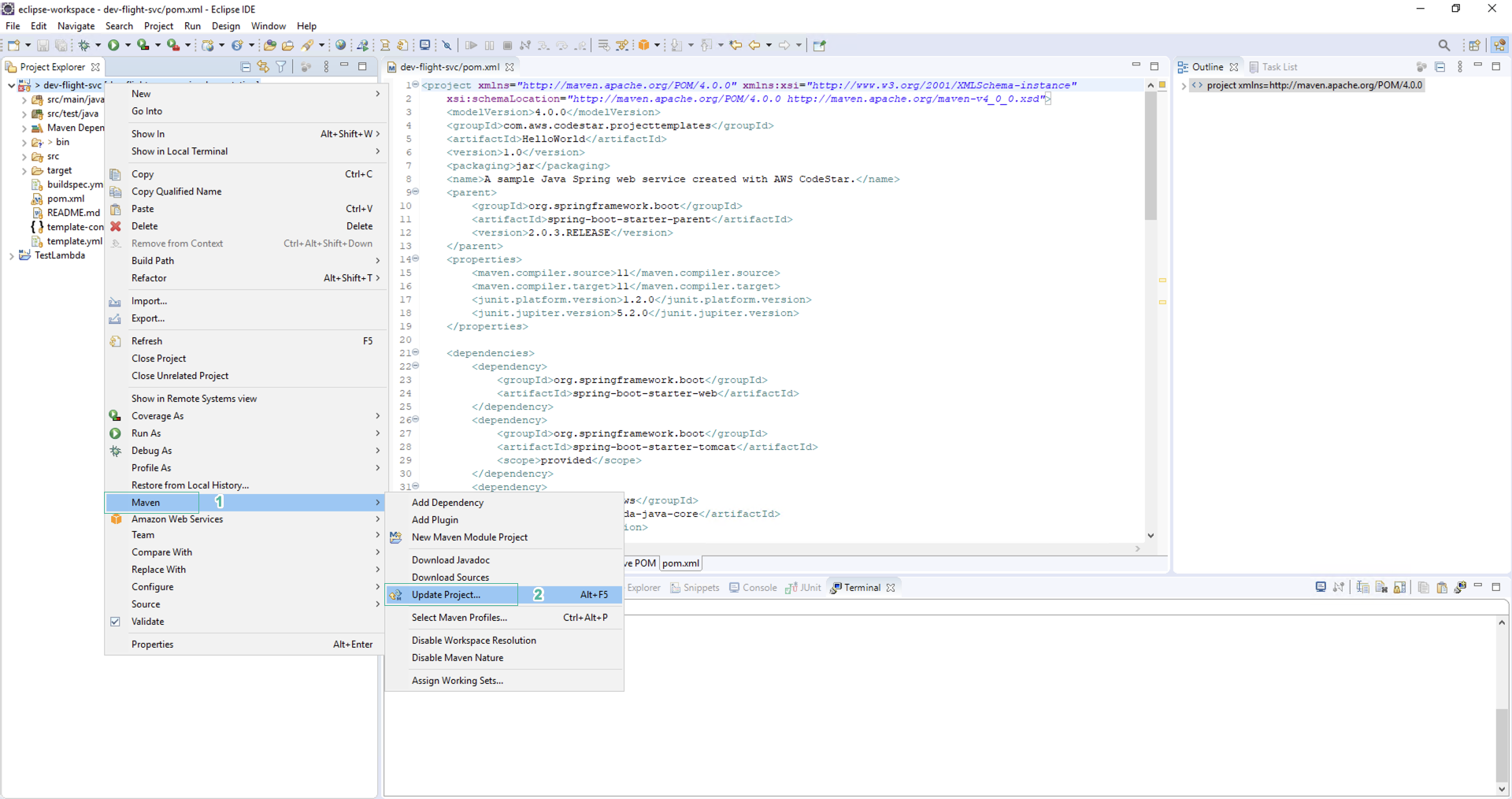
- Right-click on the project root folder, select Maven | Update Project, select OK.
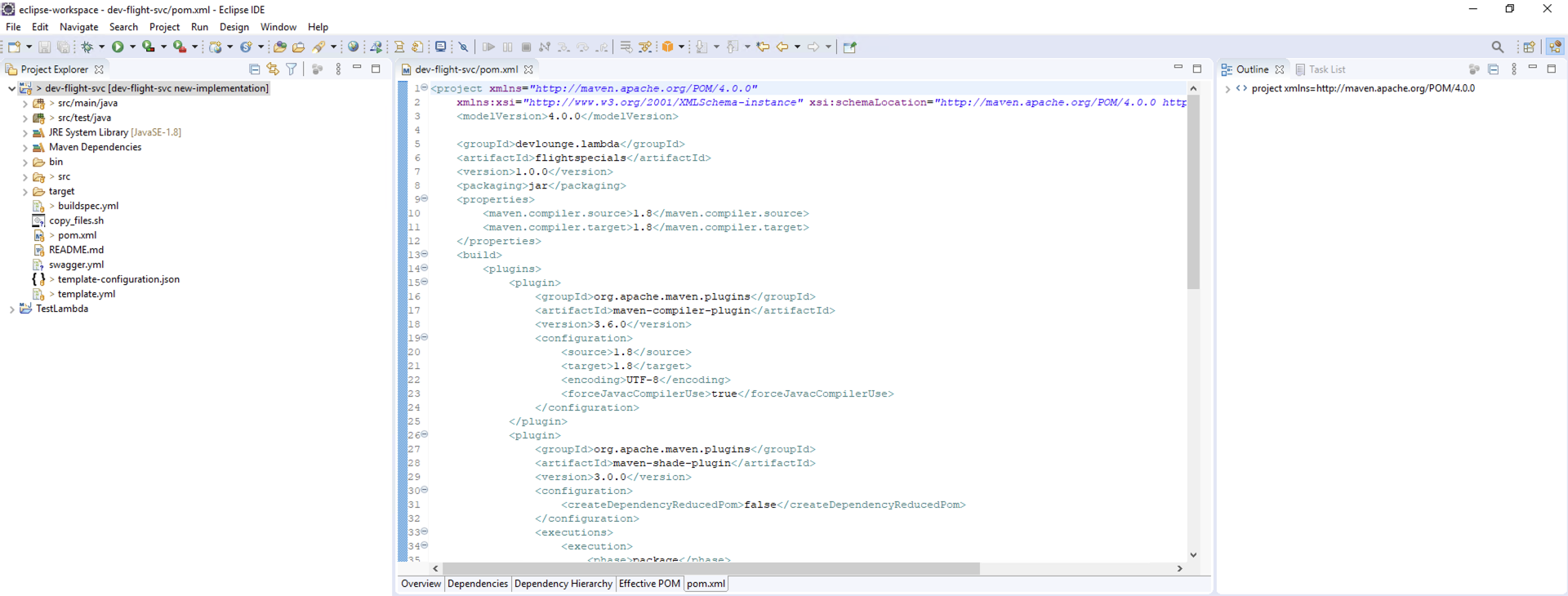
Once done, you will see the following directory structure:
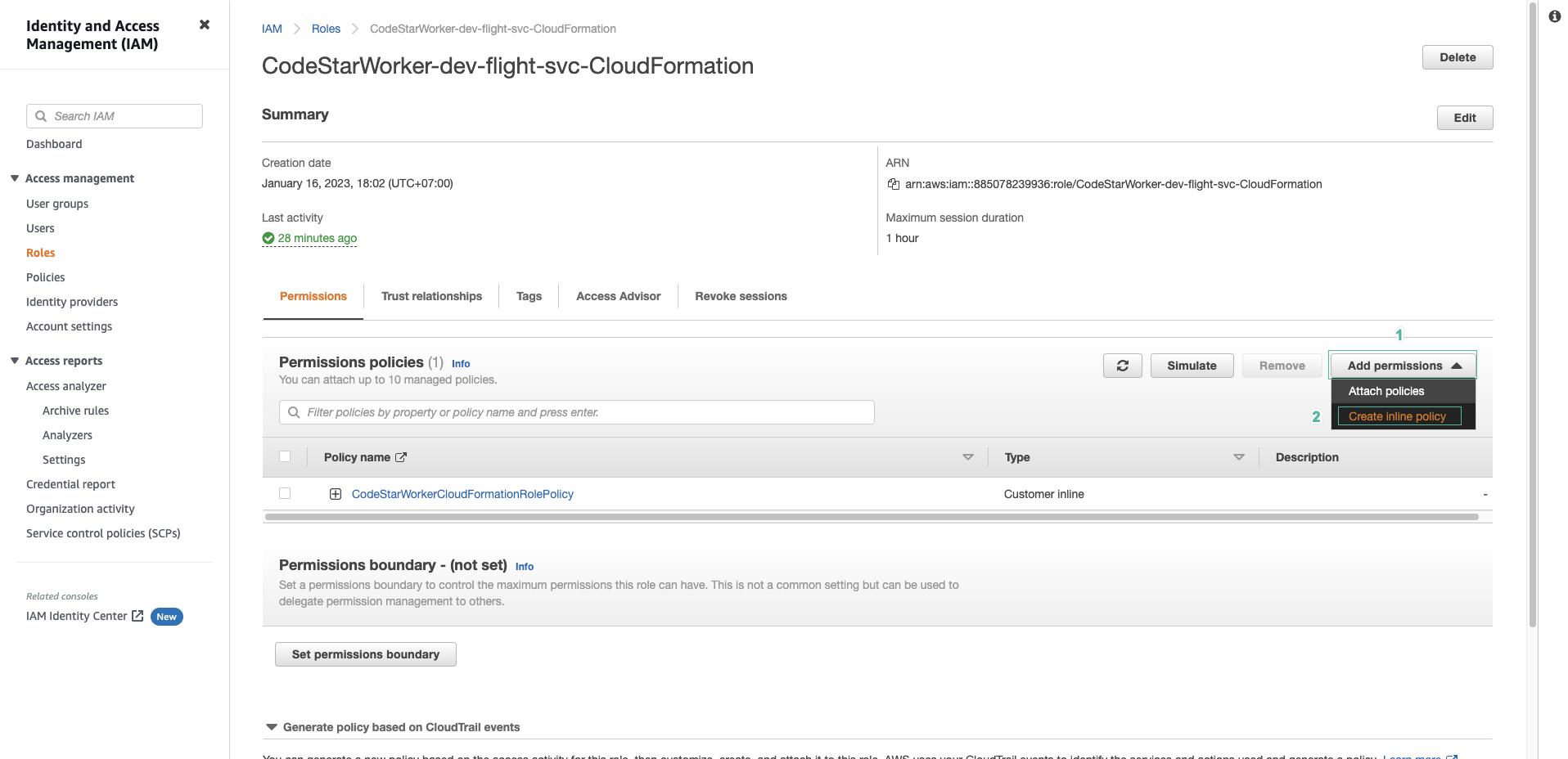
- As part of the microservice implementation, we use VPC and assign a new IAM Role to the Lambda function to allow it to perform different tasks. When CodeStar creates the project, it creates an IAM Role that grants CloudFormation permission to deploy the HelloWorld service. These permissions are not enough for higher requests, so we need to change the policy to assign permissions to CloudFormation to extend the permissions.\
- Open AWS IAM Console and select Roles.\
- In Filter box, enter CodeStarWorker-dev-flight-svc-CloudFormation to find IAM Role.\
- Open IAM role.
- Click Add permission, then select Add inline policy.
- Go to the JSON tab and paste the following code in:
{ "Version": "2012-10-17", "Statement": [ { "Action": [ "iam:GetRole", "iam:CreateRole", "iam:DeleteRole", "iam:PassRole", "iam:PutRolePolicy", "iam:DeleteRolePolicy", "lambda:ListTags", "lambda:TagResource", "lambda:UntagResource", "lambda:AddPermission", "ec2:DescribeSecurityGroups", "ec2:DescribeSubnets", "ec2:DescribeVpcs", "ec2:CreateNetworkInterface", "ec2:AttachNetworkInterface", "ec2:DescribeNetworkInterfaces" ], "Resource": "*", "Effect": "Allow" } ] }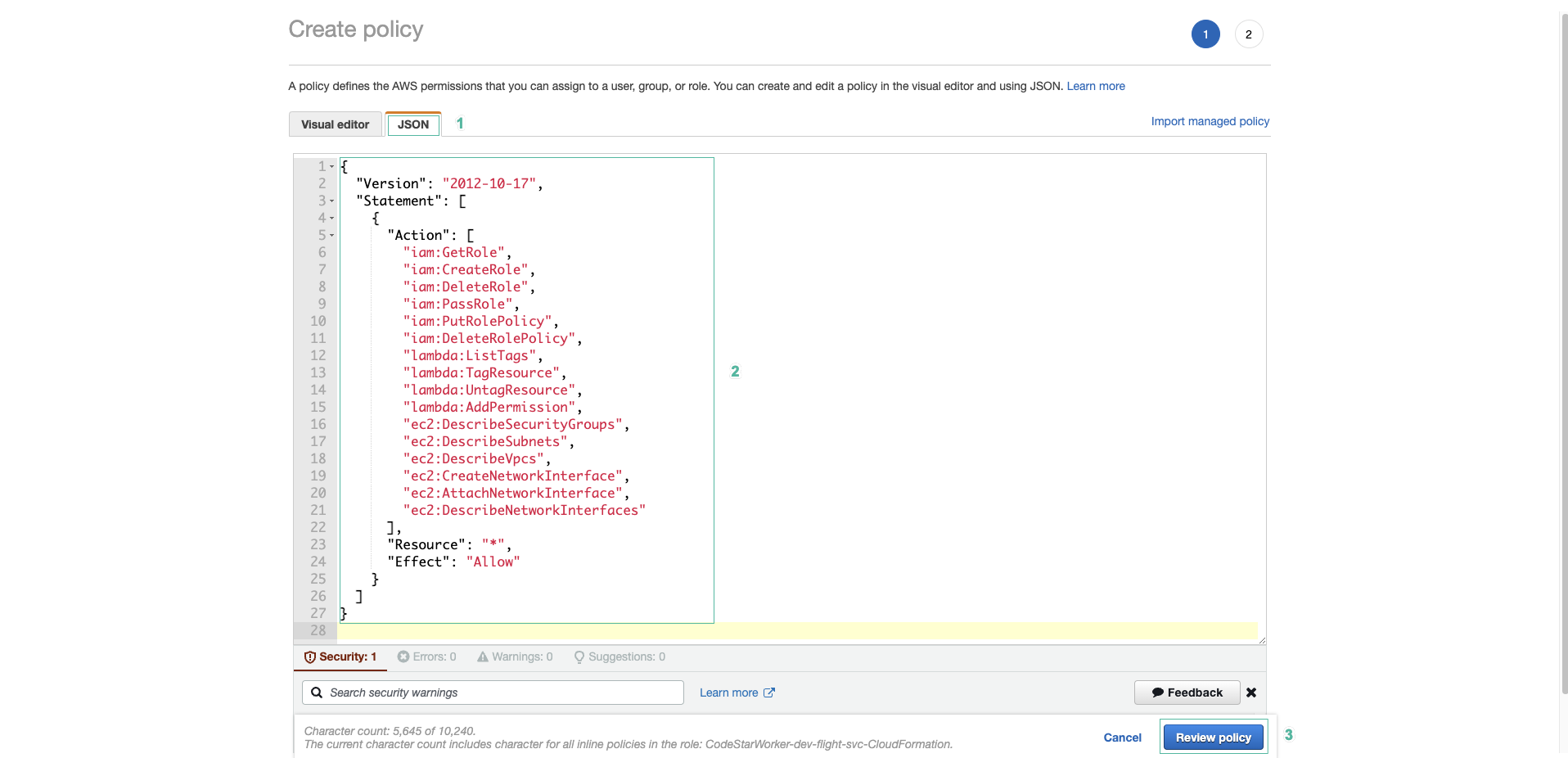
- Enter
idevelopCodeStarCloudFormationPolicyfor policy name and click Create policy.
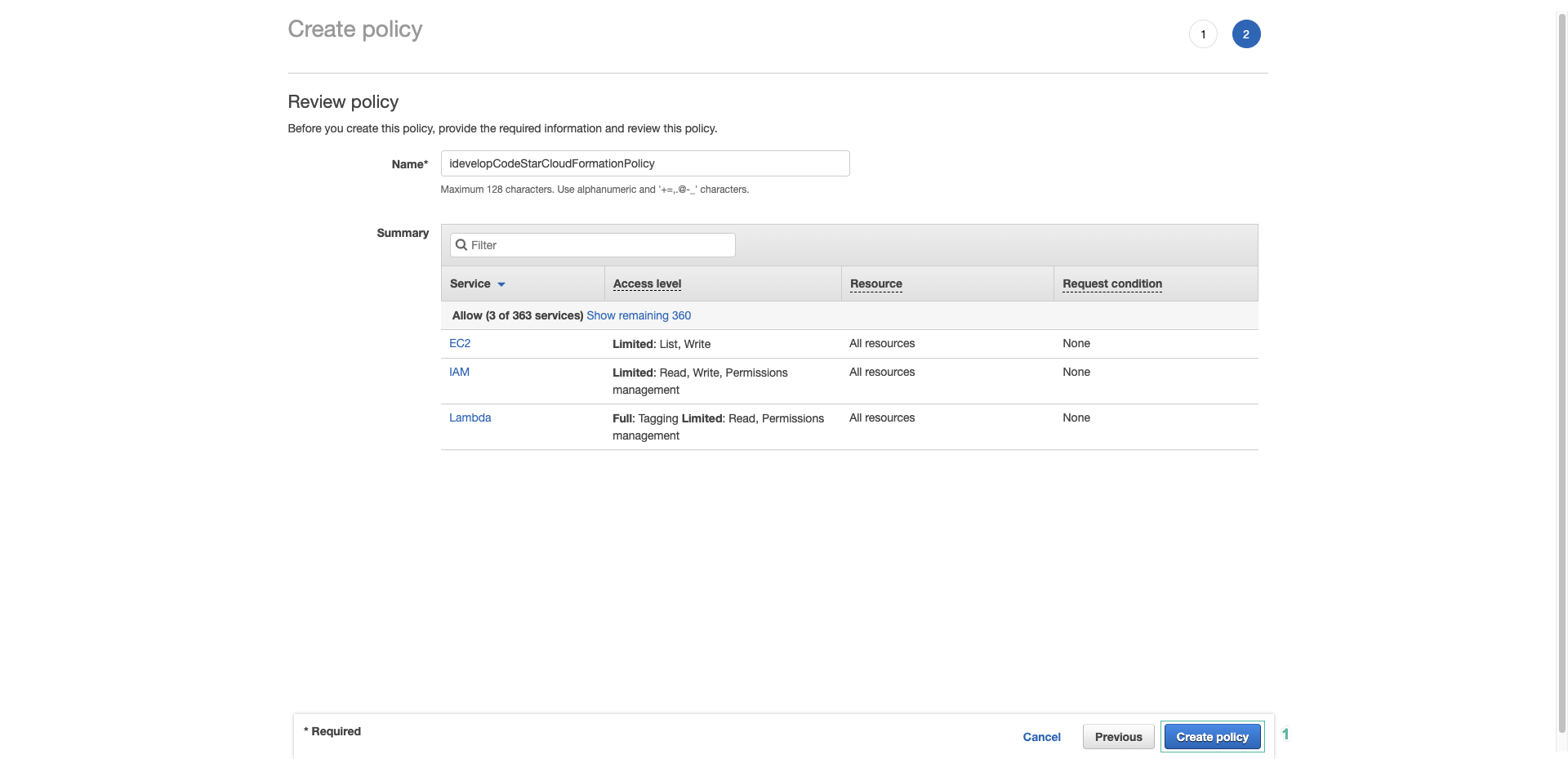
When adding the CodeStarWorker-dev-flight-svc-CloudFormation role, the permissions in the idevelopCodeStarCloudFormationPolicy policy allow CLoudFormation to act on your behalf when implementations change in the environment, including permission permissions Lambda function attached to the VPC where the RDS instance hosting the TravelBuddy website is deployed. They also allow CloudFormation to create a new IAM Role that the Lambda function uses to execute.
-
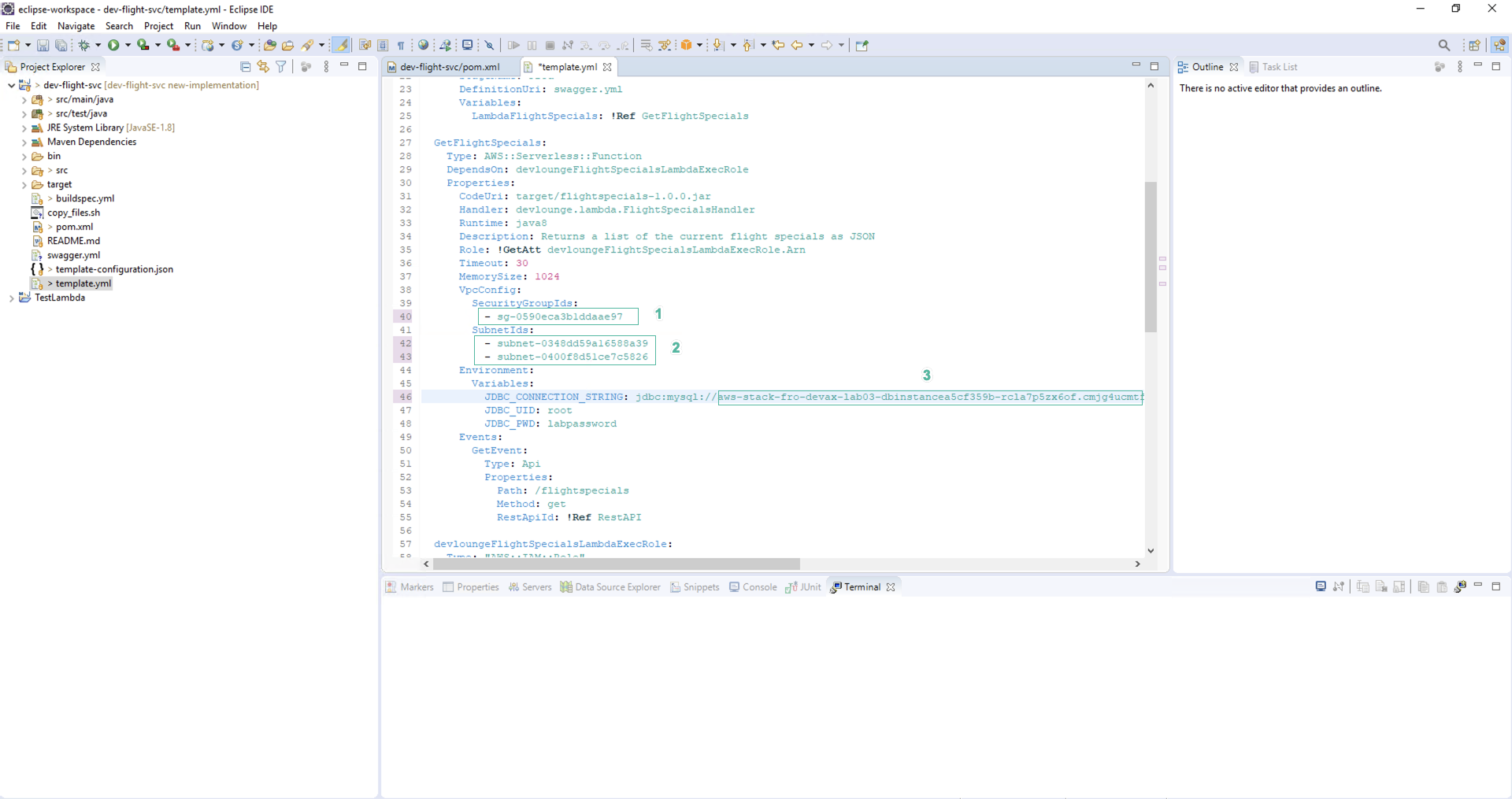
The CloudFormation template template.yml file provided in FlightSpecials.zip has several values that need updating before proceeding with deployment. These values include Subnet Ids, Security Group Ids and the RDS Instance Endpoint.
-
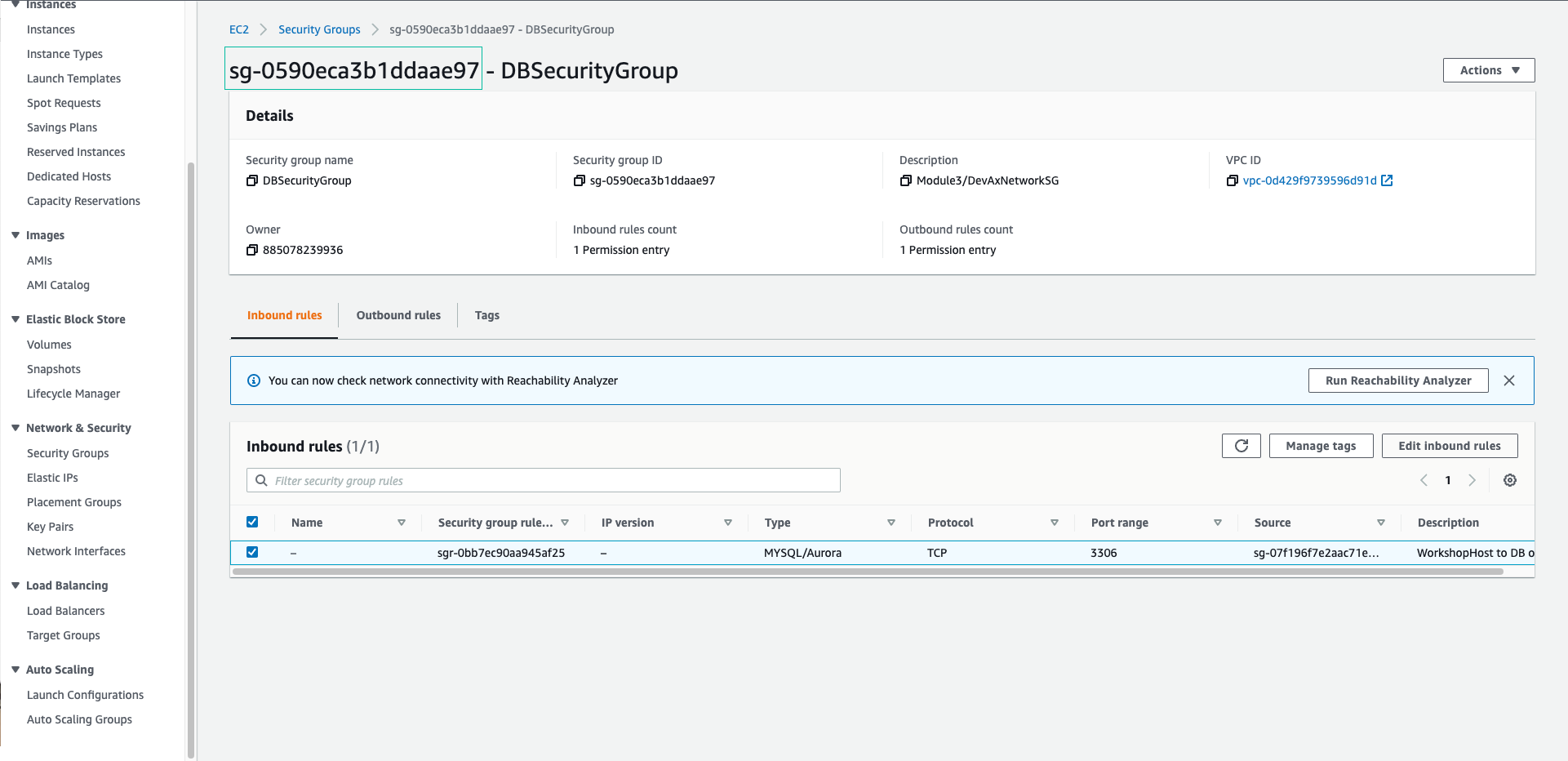
Open template.yml file and replace sg- value with Security Group Id of DBSecurityGroup.
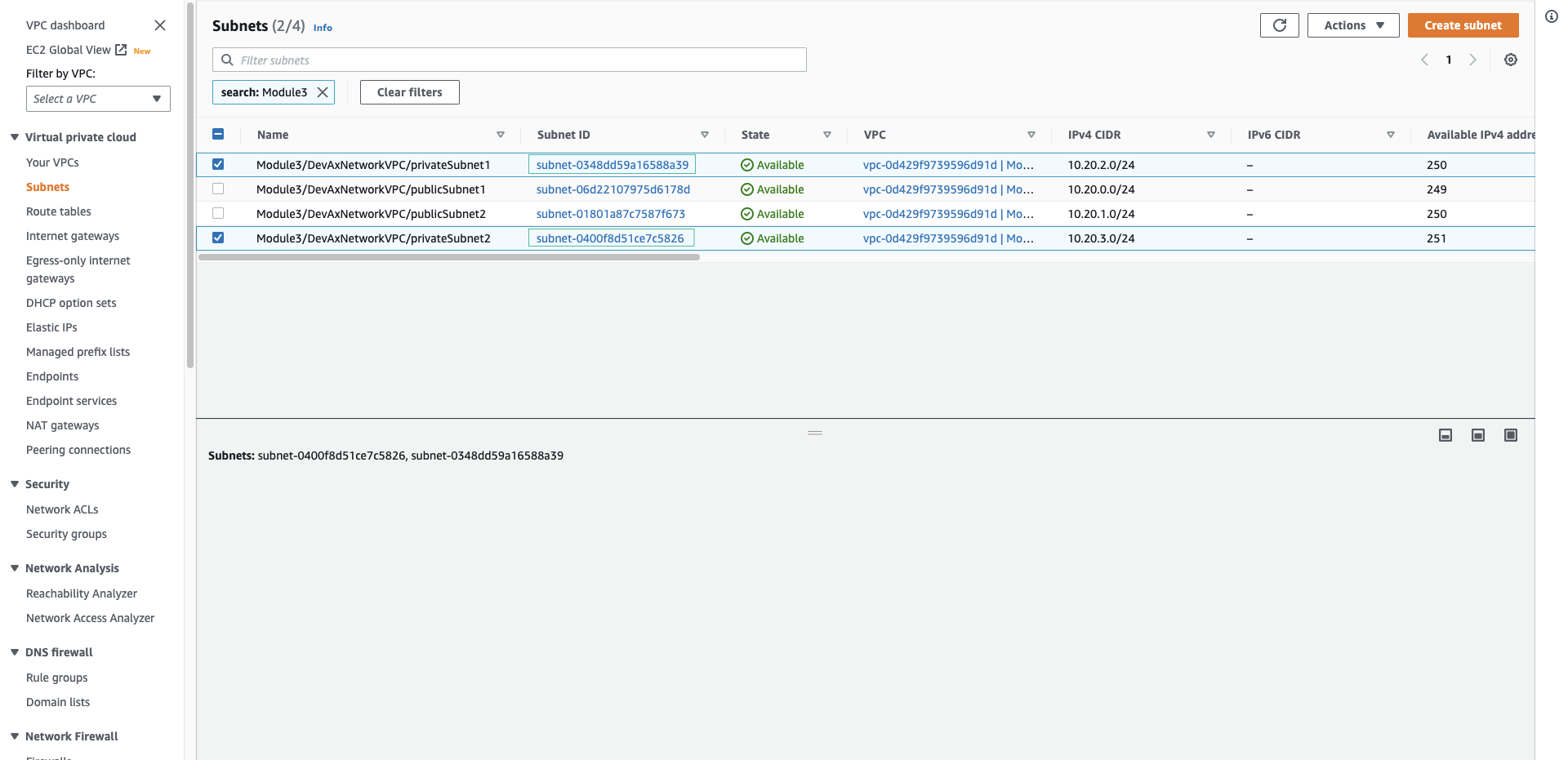
- Replace value of subnet- with 2 privateSubnet IDs named Module3/DevAxNetworkVPC/privateSubnet
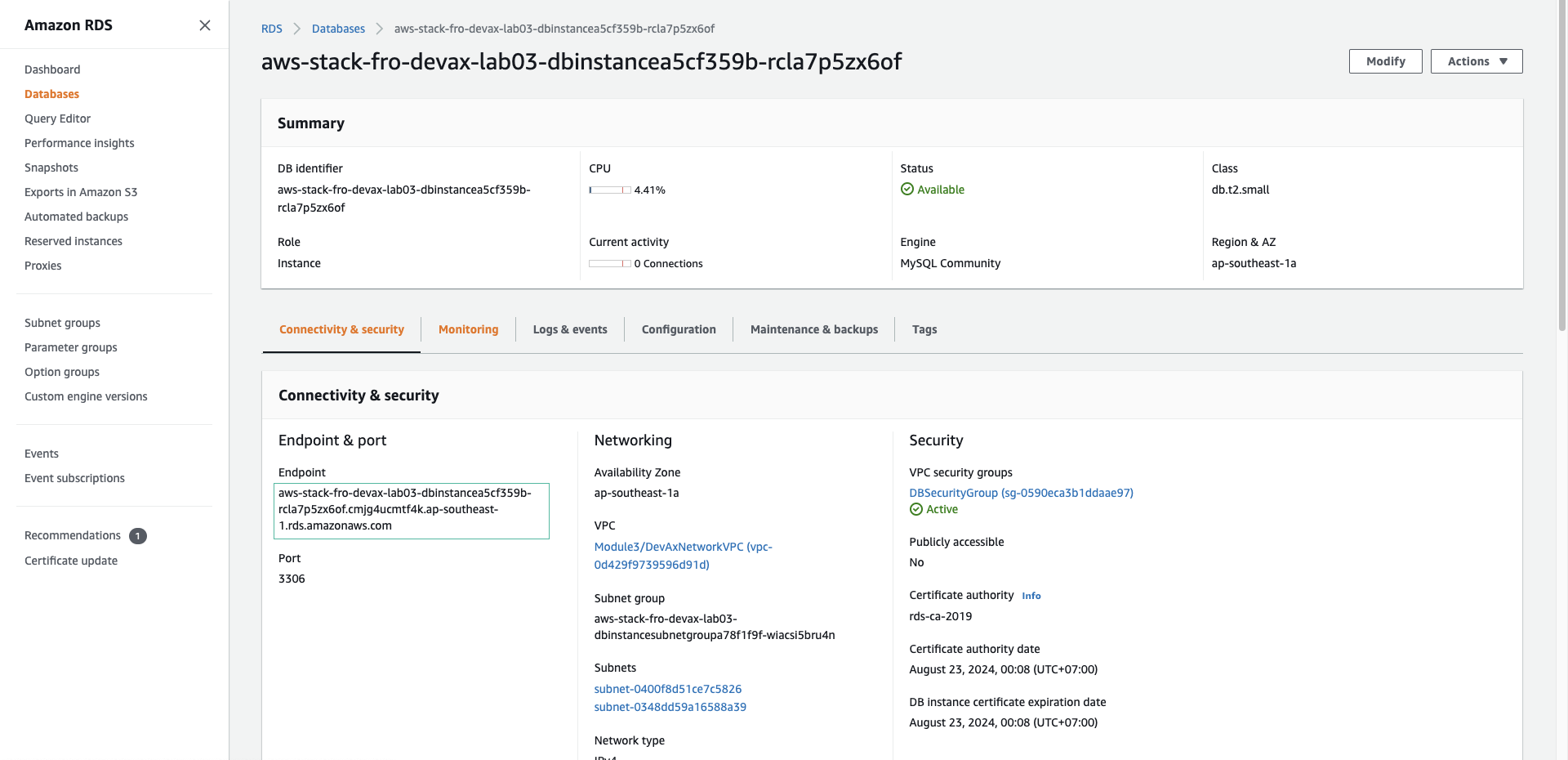
- Replace value of with RDSEndpoint that provided in the OUTPUT section of the CloudFormation or the Endpoint in the RDS instance
- When you’re done, you’ll have a VPCConfig section like this: